更多信息参考
github 地址 https://github.com/apache/apisix
文档 https://apisix.apache.org/docs/
安装
apisix-ingress-controller 与面板安装
1 | # 注释的是 gateway 方式 |
使用
简单使用 ingressClassName: apisix, 与 ingress 使用是差不多的
更多使用方法参考官网
以apisix面板为例基础使用
使用 apisix.k8s.grafana.eu.org 为地址,http 访问可以不需要证书
1 |
|
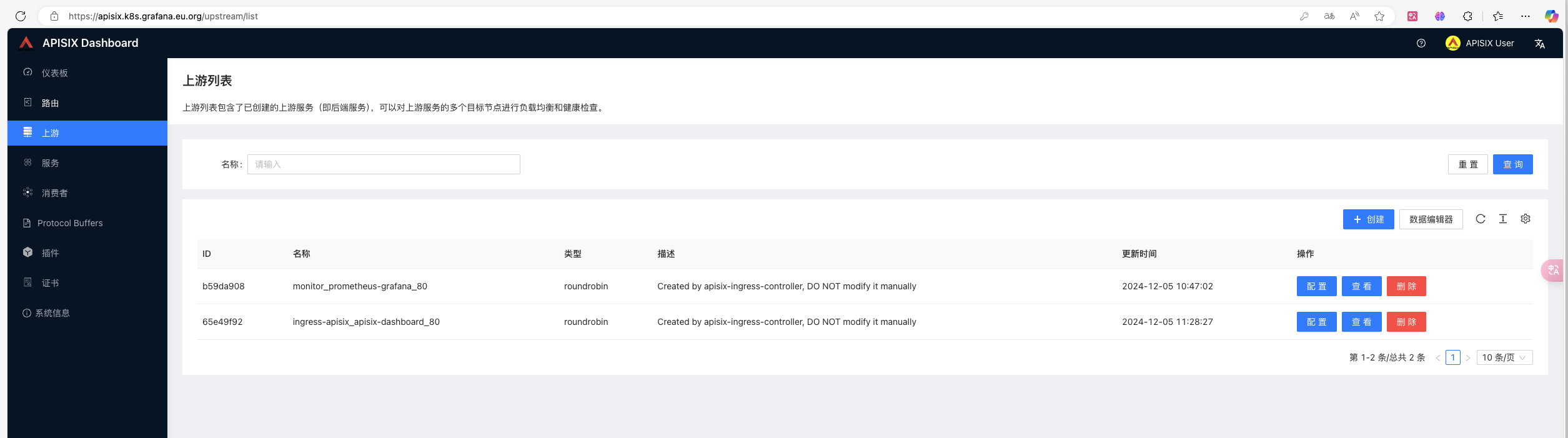
简单认证
1 | --- |
k8s-dashboard
需要定义 ApisixUpstream, 指定后端的 scheme 为 https
1 | --- |
附
1. apisix cert-manager
使用 http01 的配置也是 nginx
letsencrypt-http01.yaml
1 | apiVersion: cert-manager.io/v1 |
使用 dns01 letsencrypt-dns01.yaml1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28apiVersion: v1
kind: Secret
metadata:
name: cloudflare-api-token-secret
namespace: cert-manager # 这里配置为安装cert-manager资源的命名空间
type: Opaque
stringData:
api-token: 'xxxxxxxx'
---
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: cloudflare-acme-cluster-issuer
spec:
acme:
email: '[email protected]'
# 配置证书目录,演练环境使用Staging环境,注意区分
server: https://acme-v02.api.letsencrypt.org/directory
# server: https://acme-staging-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: acme-issuer-account-key
solvers:
- dns01:
cloudflare:
apiTokenSecretRef:
name: cloudflare-api-token-secret # 引用当前文档中创建的Secret名称
key: api-token
2. 使用通配符
创建通配符证书
1 | --- |
跨 ns 使用, ingress-nginx 不支持
1 | --- |
prometheus使用
1 | --- |